Whoever thought the Application Security (AppSec) industry does not know how to have fun has probably never attended the OWASP AppSec California conference. OWASP hosted the 2019 conference at the Annenberg Community Beach House in beautiful Santa Monica, California on January 24th thru 25th. Consider this article my review, thoughts and notes on the conference in case you ever want to attend.

The Annenberg Community Beach House is a two-story building that has a beautiful view of the beach and the pool. Photo courtesy from Miguel A. Calles, MBA.
Keynote Speakers
The keynote speakers were Adrienne Porter Felt, Engineer & Manager for Chrome at Google, and Fredrick "Flee" Lee, Head of Information Security at Square.
Adrienne shared her experience on Google requiring HTTPS on websites. She saw this transition as a way to promote modern security standards to the web industry (Check out the "Rise Of The HTTPS Bullies" Secjuice article by Guise Bule for a dissenting opinion), she also requested the audiences to help solve the problem of how to display URLs in browsers. Phishing attacks still prey on innocent individuals who may not know how to properly read a URL and the industry as a whole has done little to advance in the URL display bar since the 1994 Netscape Navigator.
Fredrick shared his view on using code reviews to drive security training, using metrics to record progress, having developers to buy into security and using them as practitioners, and refining specific goals as methods to building a successful security program at a company. He also shared some potential pitfalls: taking on too much rather than focusing on the most critical objectives and giving the program time to grow; using bad form by not having developer buying or using generic, irrelevant security training; trying to use the wrong shortcuts such as not documenting, not creating metrics, relying too much on tools, and using fear, uncertainty, and doubt to coerce developers into security. His conclusion was to start small, measure everything, encourage that everyone can do security, and being realistic that you will not build a Netflix size security program in a short time.
Presentations
There were so many interesting presentations to attend it was difficult to attend all of the ones that I wanted to see; the list of presentations and abstracts is on the AppSec Calif 2019 web site. Below are my notes on the presentations I did attend.
"Cache Me If You Can: Messing with Web Caching" by Louis Dion-Marcil
Louis stated the cache is a less known attack vector and it needs more attention by the industry. He explained how web cache deception, edge side includes, and web cache poisoning may be used in attacks. He suggested using Burp Web Cache Deception Detection, Burp ActiveScan++, Burp Upload Scanner, OWASP Mod Security Rule Set, and Burp Param Miner to detect and address those attacks.
"The White Hat's Advantage: Open-source OWASP tools to aid in penetration testing coverage" by Vincent Hopson
Vincent gave an overview on the Zed Attack Proxy (ZAP), Attack Surface Detector (ASD), Code Pulse, and Burp Suite Pro tools. He gave a demonstration on using ZAP on a vulnerable web site and how ASD can be used to get better results in ZAP.
"Lightning Talk: Building Cloud-Native Security for Apps and APIs with NGINX" by Stepan Ilyin
Stepan explained how to take advantage of the Web Application Firewall (WAF) features provided by the NGNIX webserver software. The WAF is enabled using the NGNIX mod_security feature. This feature can be coupled with Elasticsearch for searching, and 444 error codes to help prevent against Distributed Denial of Service (DDoS) attacks. He also recommended using the Google Cloud Platform, Amazon Web Services, and Azure list of IP ranges to block requests from undesired country origins.
"Startup security: Starting a security program at a startup" by Evan Johnson
Evan shared his experience on starting security programs at the three startups where he has worked. He summed up security at startups to four main points: relationships, security culture, compromise, and continuous improvement. He shared his security playbook on aspects of security that can be completed within a fiscal quarter: security engineering, detection & response/incident response, compliance, and corporate security. His key takeaways included: focus on the things you can complete, focus on the most significant problems, avoid high maintenance tasks, and whether you are more secure than the previous month.
"Lighting Talk: Node.js and NPM ecosystem: what are the security stakes?" by Vladimir de Turckheim
Vladimir started the talk by explaining Node and the NPM ecosystem. He highlighted the more obvious attack vectors: SQL injections, NoSQL/SQL object injections, and Regular Expression Denial of Service (ReDOS). He transitioned to an attack surface which can affect the end-user, the repositories, continuous integration/development servers, and the developers: the NPM ecosystem. He used the 2018 ESLint malicious package attack as an example of how a package within the ecosystem can be used to run malicious code. He recommended knowing which packages are used and minimizing the depth of the dependency tree with tools such as NodeSource, the Anvaka package visualizer, and Sqreen.
"The Art of Vulnerability Management" by Alexandra Nassar
Alexandra shared her experience in implementing a strong vulnerability management program in her company. She worked with the developers to use their existing workflows, terms, and tools to establish the program. This meant using Jira to tracking vulnerabilities and seeing them to completion. She narrowed down the program to three fundamental principles: self-service, accountability, and culture. She wanted the developers to be involved in the security program, she collected metrics, and she marketed security by introducing champions and having a funny unicorn for her security logo.
"An Attacker's View of Serverless and GraphQL Apps" by Abhay Bhargav
Abhay started by giving the audience an overview on Serverless and GraphQL. He then showed multiple demonstrations using the DVFaaS - Damn Vulnerable Functions as a Service to show how Serverless and GraphQL can be attacked. In one demonstration, he showed how using a nested GraphQL query sent to a Serverless function would take several seconds, thus translating into a $3 charge from the provider; in a DDoS attack, this could become several thousands of dollars. Although he praised both frameworks, he warned both require do-it-yourself security and thus create inherent vulnerability the application.
"On the Frontlines: Securing a Major Cryptocurrency Exchange" by Neil Smithline
Neil shared the high-level security architecture of his exchange service and shared real-world examples of the attacks his company faces. I was amazed by how many layers of security his company needs to use to protect against multiple attack vectors. They do not use text messaging for Two Factor Authentication (2FA) because phone porting is so easily; he recommended Google Voice if you use 2FA. They require two Google Authenticators and physical tokens such as YubiKey. They run the wallet software in containers because they are third party services and their repositories might get compromised. They store the majority of the wallets in cold storage and only have a small subset in hot storage, to avoid a total loss in the event of a breach. They also have strict protocols against social engineering attacks.
Vendor Expo

The Annenberg Community Beach House has a nice pool. The vendor booths and lunch were staged around the pool. Photo courtesy from Miguel A. Calles, MBA.
I met nice vendors with capable products. I spoke with Netsparker, CodeDx, Snyk, WhiteSource, Security Compass, and CheckMarx. There were many more vendors I was unable to visit.
Capture the Flag (CTF) Event

There is a patio to the side of the Annenberg Community Beach House where you can relax, eat, and see the scenic view. Did I mention the event also hosted a Capture the Flag event? Photo courtesy from Miguel A. Calles, MBA.
During the entire conference, there was a CTF where anyone can come and participate at any time. This was my first CTF experience. I stopped in one hour and 40 minutes before the event closed and only played for one hour. The goal was to find and exploit as many vulnerabilities in a fictitious banking and stock trading web site.
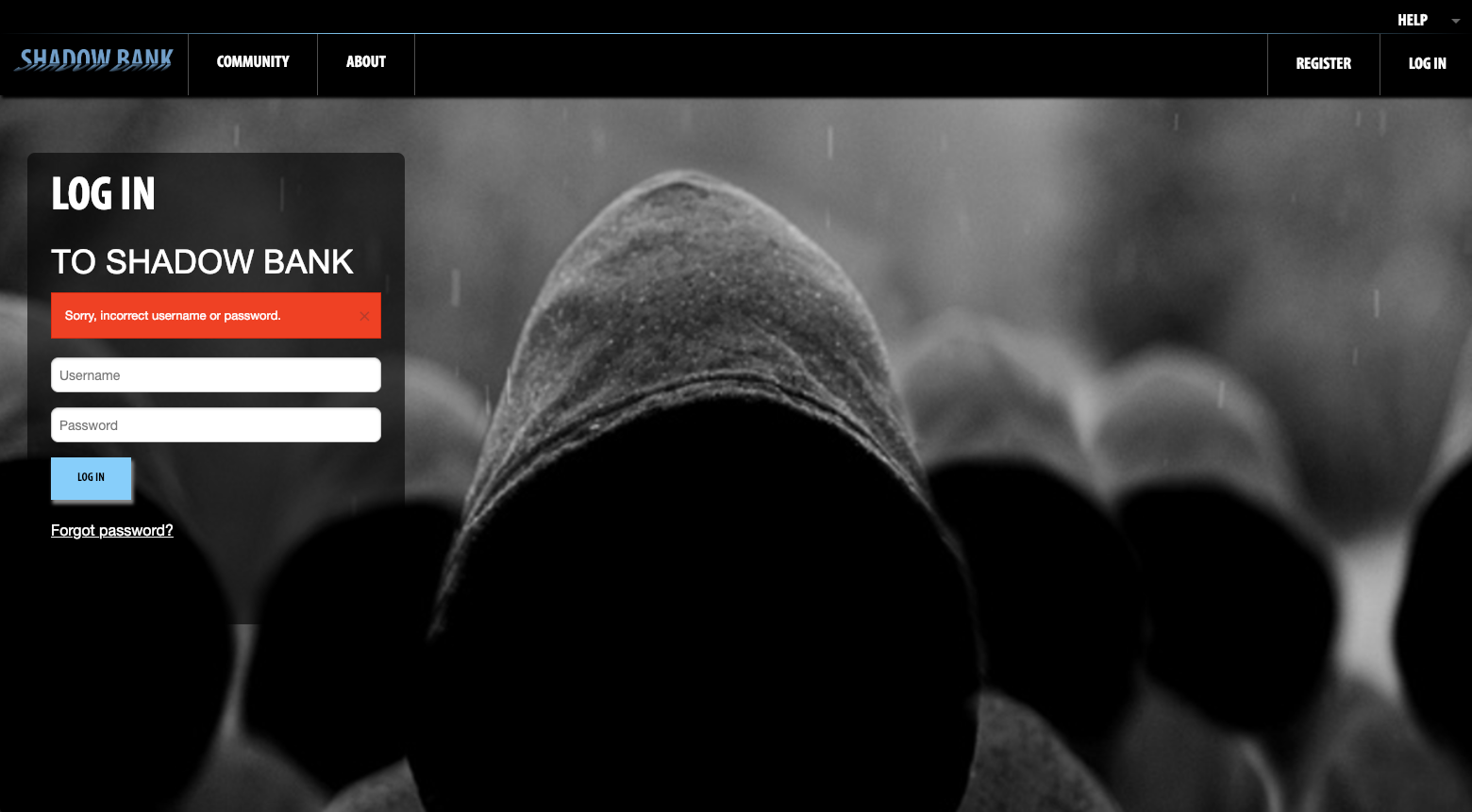
The fictitious banking web site created by the OWASP AppSec California conference committee.
I went for an hour and decided I would not ask for help. I wanted to see how well I fared. I was able to perform cross-site script (XSS) attacks on multiple pages, an SQL injection attack, and sell stock I did not own (to make a nice profit). After about an hour, I left to attend the last presentation of the day. I ranked 25th place with only 40 minutes left in the competition; not bad for a newbie to CTF.
Observations
I enjoyed the conference, it was well organized and the community was nice, I thought that he location was wonderful and that the food was delicious. There was a good diversity in the speakers: both men and women, both keynote speakers were under-represented groups, different ethnicities, and all were very knowledgeable with different perspectives.
I do believe the industry could benefit from a higher women-to-man ratio; this is based on the ratio of the attendees. The women presenters brought an interesting perspective and approached the soft skills needed in the industry differently.
Having more diversity of thought will greatly advance the AppSec industry.
Conclusion
I recommend attending the OWASP AppSec California conference if you are able. I had wanted to attend for a few years, and I enjoyed it. I believe anyone interested in learning about security would benefit, whether or not that person is a software developer, security engineer, or knowledgeable in security.
You may be wondering...
Did I meet Mr. Robot? I did not, but he's now singing Bohemian Rhapsody. (It looks like a great movie from the previews!)
Was I hacked? No, but I got to feel like a hacker during the CTF event.
Did I learn anything new? Yes! I learned a lot of stuff, especially from "Cache Me If You Can: Messing with Web Caching" by Louis Dion-Marcil.
Did anyone fall into the pool? Not that I saw, but there was one guy swimming by himself during the lunch hour on the last day and everyone was watching him swim :)
Before you go
About the author
Originally published on Secjuice.com
Image by Mohamed Chahin on Dibbble

